Steps to Create Certificate Template
Step 1
Open the Certificate Authority Tool:
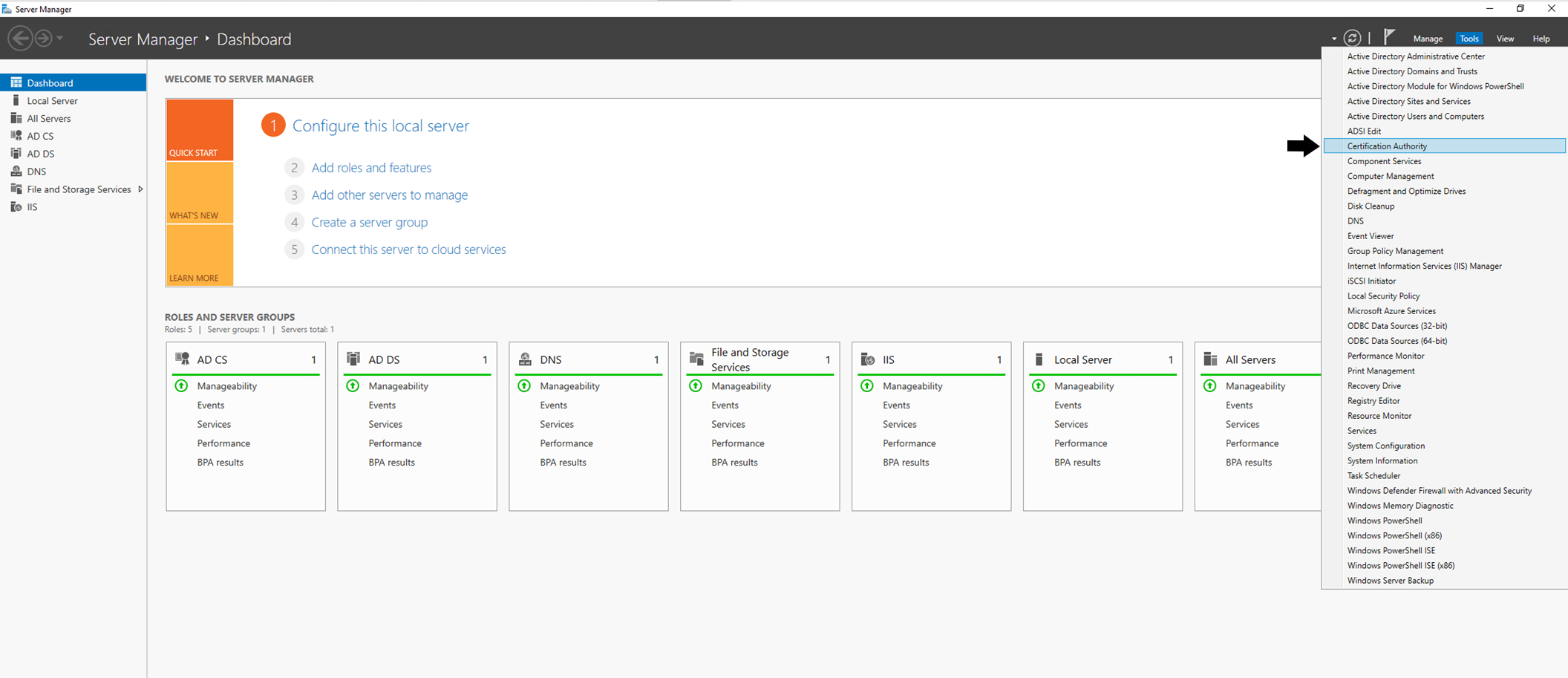
Step 2
Expand the tree on the left and Right Click on Certificate Templates and select Manage:
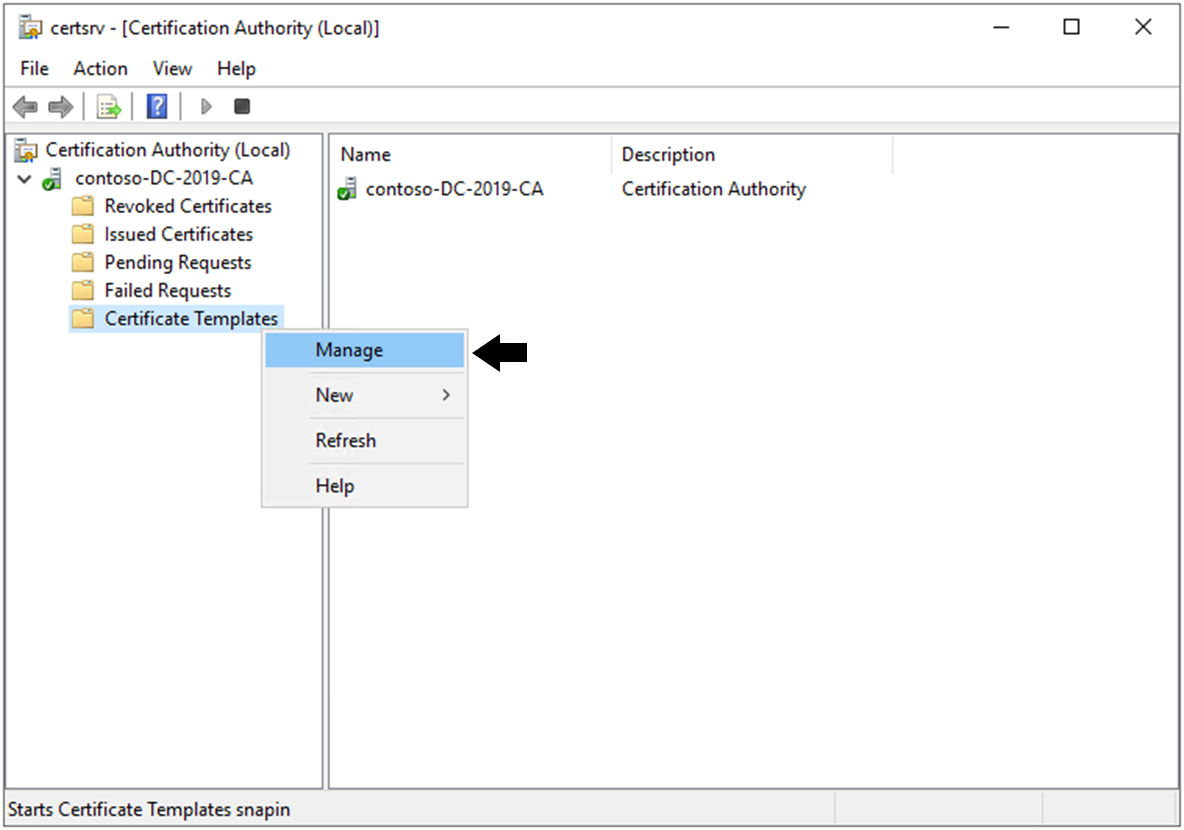
Step 3
Right Click on the IPSec (Offline request) template display name, and select Duplicate Template:
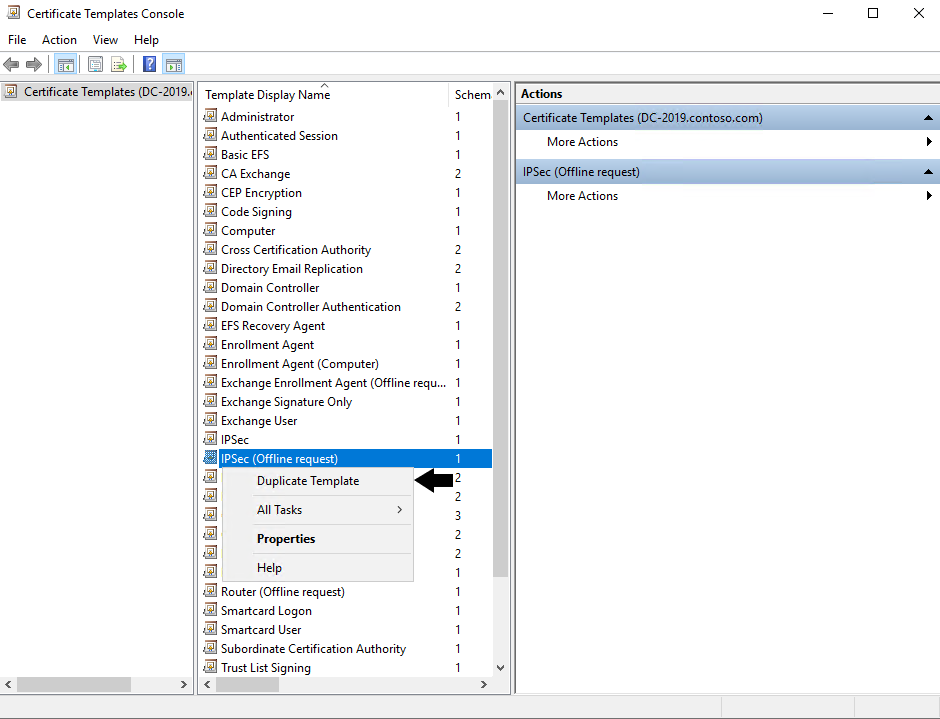
Step 4
Confirm the Compatibility tab:
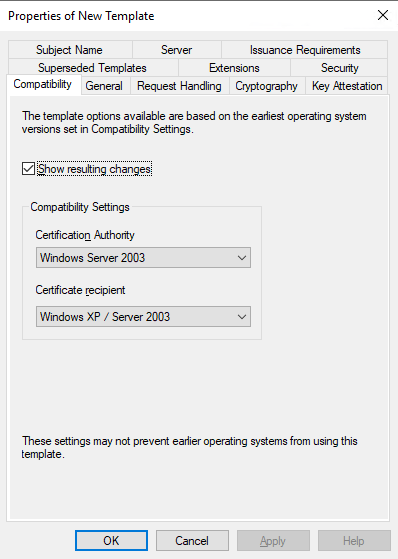
Step 5
Confirm you have modified the following in the General tab:
-
Template Display Name:
System Center Operations Manager -
Validity period:
5 years(change this per your security policy) - Check
Publish certificate in Active Directory
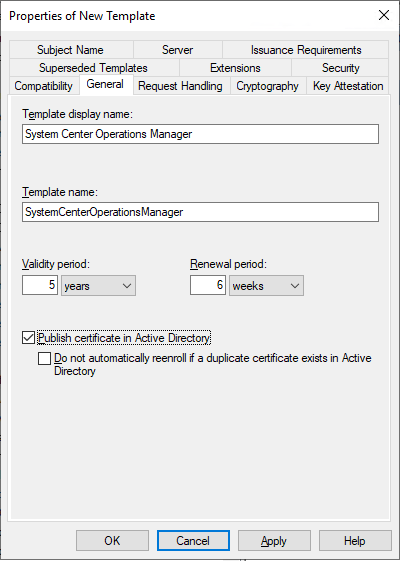
Step 6
Confirm you have modified the following in the Request Handling tab:
- Check Allow private key to be exportable (this is required for Server Authentication)
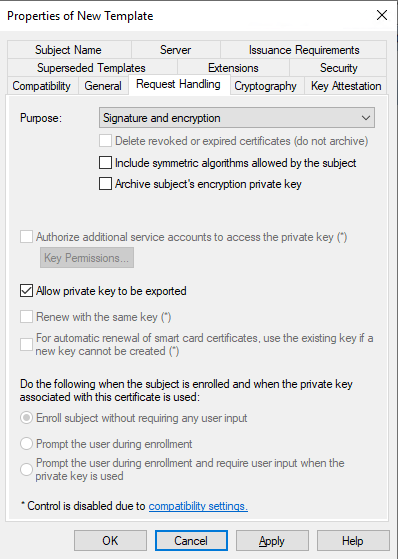
Step 7
Confirm you have modified the following in the Cryptography tab:
- Verify Microsoft RSA SChannel Cryptographic Provider is Checked
- Under Providers Check Microsoft Enhanced Cryptographic Provider v1.0 and move it to below Microsoft RSA SChannel Cryptographic Provider
- Verify Minimum key size is set to
2048or1024(2048 adds CPU overhead)
Step 8
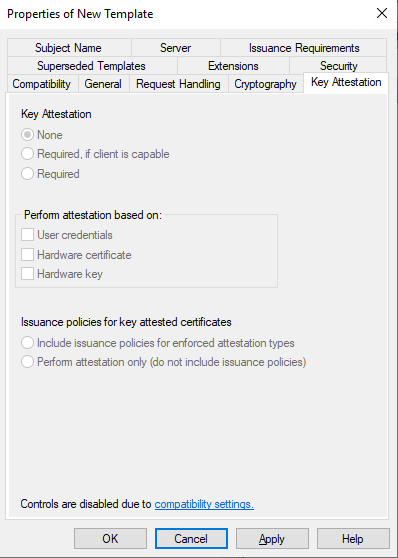
Confirm that None is selected for the Key Attestation tab:
Step 9
Confirm you have modified the following in the Extensions tab:
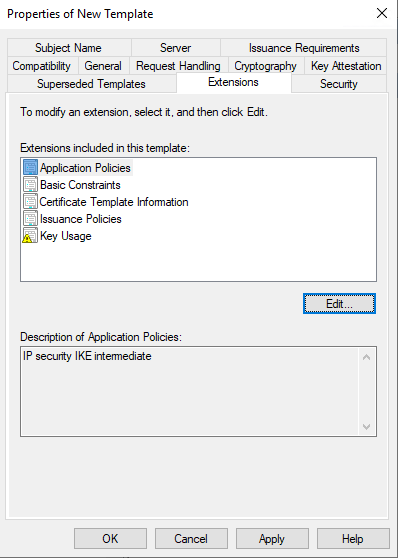
- Click on Application Policies and Edit
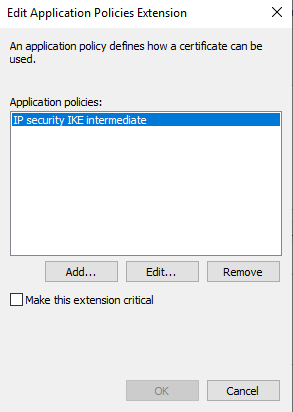
- Remove IP security IKE intermediate
- Add:
- Client Authentication
-
Server Authentication
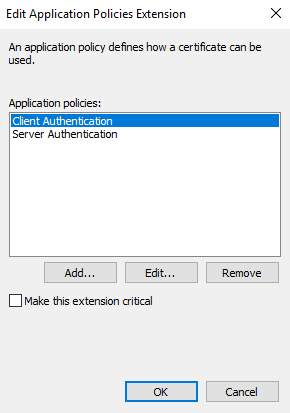
- Click OK
- Remove IP security IKE intermediate
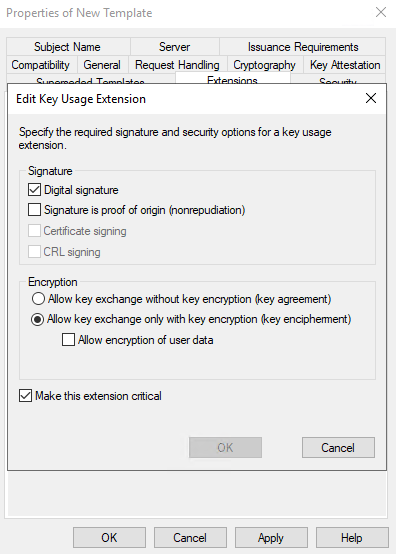
- Click on Key Usage and Edit
- Confirm you have checked:
- Make this extension critical
- Click OK
- Confirm you have checked:
Step 10
Confirm you have modified the following in the Security tab:
- You can add multiple types of objects here: Users, Computers, Service Accounts, Groups, or Built-in security principals.
For simplicity I will keep the defaults and only add the following permissions on Authenticated Users:- Read
-
Enroll
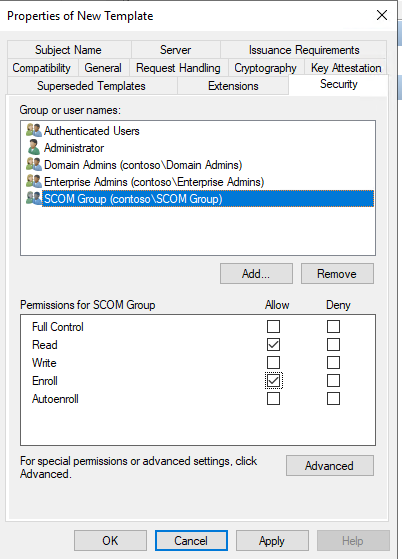
- Click OK to confirm / create the Certificate Template
Step 11
Close the certificate templates Console.
- In the Certificate Authority tool, right click on Certificate Templates
- Hover over New -> Select Certificate Template to Issue
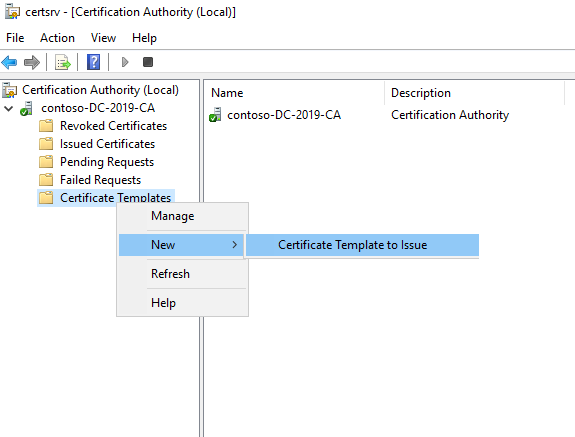
- Select the Certificate Template Display Name you created in Step 5:
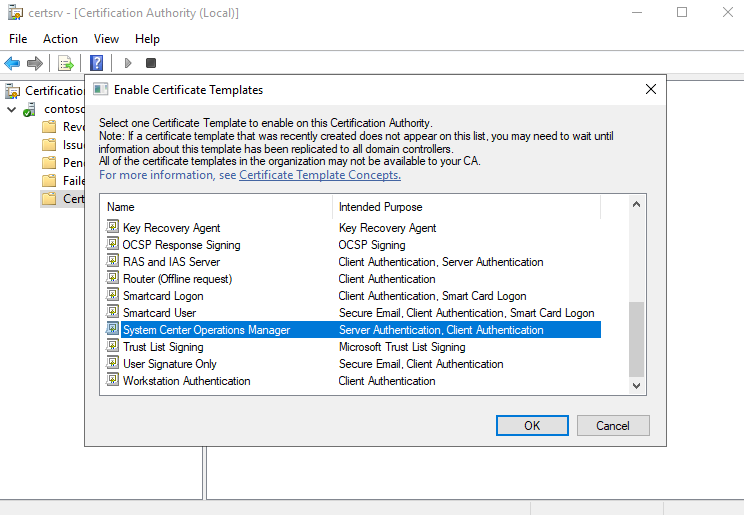
- Click OK
- Hover over New -> Select Certificate Template to Issue
Step 12
Verify you are seeing the Certificate Template on your Management Server.
- Open Local Machine Certificate Store:
certlm.msc - Open Personal -> Certificates
- Right Click Certificates and hover over All Tasks -> Select Request New Certificate…
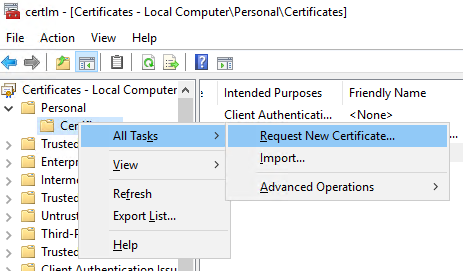
- Skip through the first screen
- Click Next
- Verify that you have selected Active Directory Enrollment Policy
- Click Next
-
Select the checkbox next to the Certificate Template you created and click on the Warning sign below the Certificate Template, it says click here to configure settings.
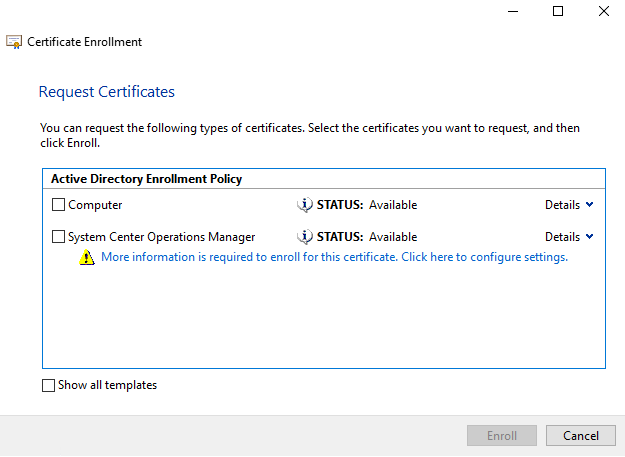
- Example of how to configure the certificate to be used by a Management Server
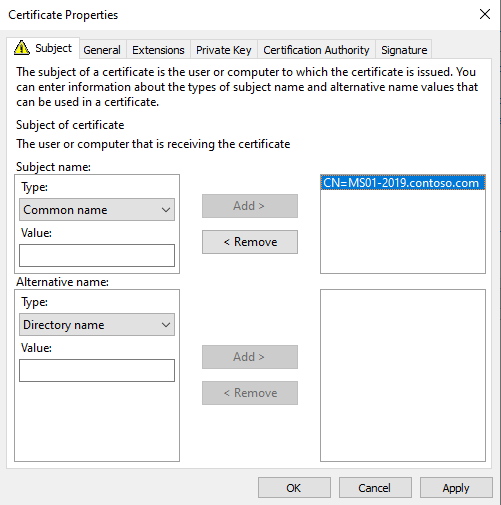
- Click OK
- Click on Enroll
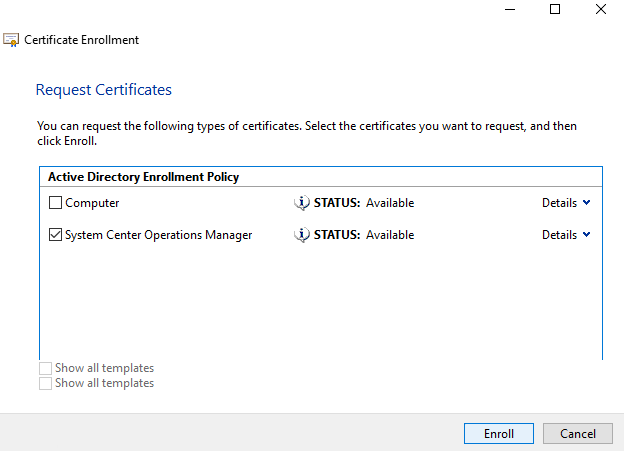
- Skip through the first screen
Step 13
In order to use certificates with System Center Operations Manager you will need to generate / perform run the MOMCertImport tool on atleast one of the Management Servers, and any servers that will communicate via Certificates (DMZ servers, Workgroup Machines, etc.).
-
MOMCertImport.exeis located in your System Center Operations Manager Installation Media inside ofSupportTools\AMD64.- Right Click on
MOMCertImport.exeand select Run as administrator- Select the certificate you generated via the System Center Operations Manager Certificate Template.
- Right Click on
Step 14
Restart the Microsoft Monitoring Agent with the following Powershell Command:
Restart-Service HealthService
After restarting the Microsoft Monitoring Agent (HealthService). You will wait until you see the following Event (Event ID: 20053) in the Operations Manager Event Log confirming that the certificate has been loaded:
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 2/28/2022 10:35:36 AM
Event ID: 20053
Task Category: None
Level: Information
Keywords: Classic
User: N/A
Computer: MS01-2019.contoso.com
Description:
The OpsMgr Connector has loaded the specified authentication certificate successfully.
Important
You may experience issues when a certificate Re-enrolls automatically. Operations Manager needs the certificate to be imported with MOMCertImport.exe prior to being able to be used by SCOM. Unfortunately, there is not an automated method for SCOM Certificate Management.
Note
You may experience issues with connectivity between the remote machine and the Management Server(s), verify you have checked these things:
- Ensure all SPN’s are correctly registered for Management Servers, Operations Manager & Data Warehouse Databases, and services that are utilizing them.
- Event ID
20071and21016on Gateway point to Firewall, SPN, or Certificate issue in most cases.- Run the Gateway Approval Tool using the SDK (Data Access Service) account OR an account with high permission level (SysAdmin privileges) to Operations Manager SQL DB.
- Verify you selected the appropriate certificate when you run MOMCertImport, check the certificate properties.
- You may also check the following registry path:
HKEY_LOCAL_MACHINE\Software\Microsoft\Microsoft OperationsManager\3.0\Machine Settings
- Check the key:
ChannelCertificateSerialNumberthis is the serial number of the certificate you imported, reversed.- Verify that there are not any other certificates in the Local Machine Personal Store that have matching Subject Names.
- Operations Manager only uses the first CN name in the Subject of the Certificate.
- Cryptography API Key Storage Provider (KSP) is not supported for Operations Manager certificates.
Share on:
